CryptoLocker Prevention: Top 12 Defenses Against Business Loss
Despite worldwide publicity concerning the staggering business loss from CryptoLocker (or other variants), few organizations have taken precautions to protect themselves.In this business advisory, we will share the top previously undisclosed methods of avoiding lost revenues and bad publicity due to ransomware.
Warning: You won’t see the basic computer usage tips for CryptoLocker prevention from Homeland Security or technology news sites – have a backup, run anti-virus, don’t open attachments, and practice safe web browsing.
1. Know CryptoLocker Realities and Myths
You get CryptoLocker and similar viruses through:- Opening Zip attachments from hoax or SPAM e-mails disguised as legitimate business correspondence (see Trend Micro Crypto SPAM example).
- Drive-by-downloads while browsing the web without clicking any links or accepting a file download.
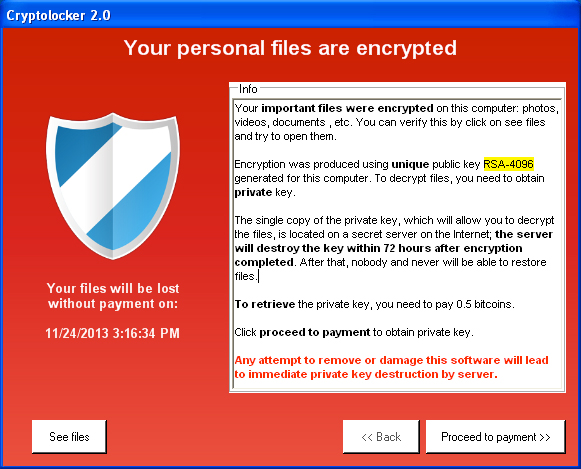
Once infected, CryptoLocker does the following as fully described in the CryptoLocker Guide by Bleeping Computer:
- Creates an auto-start entry in the registry to hijack EXE file associations, so any program you run deletes any shadow copies to prevent local restore.
- Locates and communicates with a command and control server to obtain a public key to encrypt your data.
- Scans all physical and network drives for common data file extensions and then encrypts the files making them unusable.
- Displays the CryptoLocker screen demanding a ransom of $300 paid via bitcoin within 72 hours to receive a private key to decrypt your data.
- Regardless of updates or type of anti-virus, CryptoLocker usually cannot be detected until it has already infected a computer.
- Most anti-virus and malware prevention tools will remove CryptoLocker, but data files will remain encrypted and unusable.
- New variants of ransomware mean a Mac is just as vulnerable and hackers leverage Apple’s own encryption.
- Having files encrypted with Bitlocker will not prevent you from being infected by CryptoLocker.
- While the FBI has arrested a prominent hacker of a Russian crime syndicate, CryptoLocker is still rampant.
- CryptoPrevent is available from FoolishIT, but should not be considered as a replacement for common security.
- FireEye has developed a web portal to decrypt infected files, but the utility does not work with all CryptoLocker variants.
2. Block EXE file attachments in Office 365
The easiest and most effective way to block the CryptoLocker virus in Office 365 is to block all attachments that contain EXE files (including zip files):- Logon to Office 365 as an administrator.
- Click Exchange under Admin menu at the left.
- Click Mail Flow menu option.
- Create a new rule called Block Executable Content.
- Click More options to see available rule choices.
- Apply the rule to any attachment that has executable content.
- Automatically delete the message with no notification.
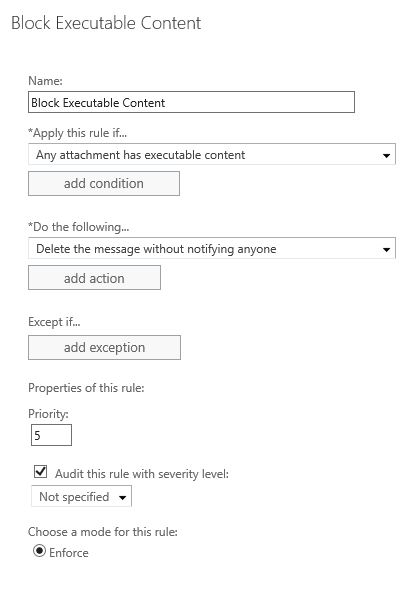
Office 365 represents about 70% of e-mail services on the Internet, but similar options may be set in other popular SPAM filters. There is virtually no reason to receive executable files by e-mail, but you’ll notice you can provide exclusion conditions if desired. To prevent unnecessary concern over administrative SPAM, any notifications should be disabled just like when viruses are blocked.
3. Activate Web Filtering for Malicious Sites
Web filtering is a controversial issue because many applications show continuous Internet connections, so it is impractical to determine how long someone is on the web. There is also a conflict between business tasks and personal activities. However, no one wants malware and most firewalls offer web filtering by category to automatically block known security risk sites.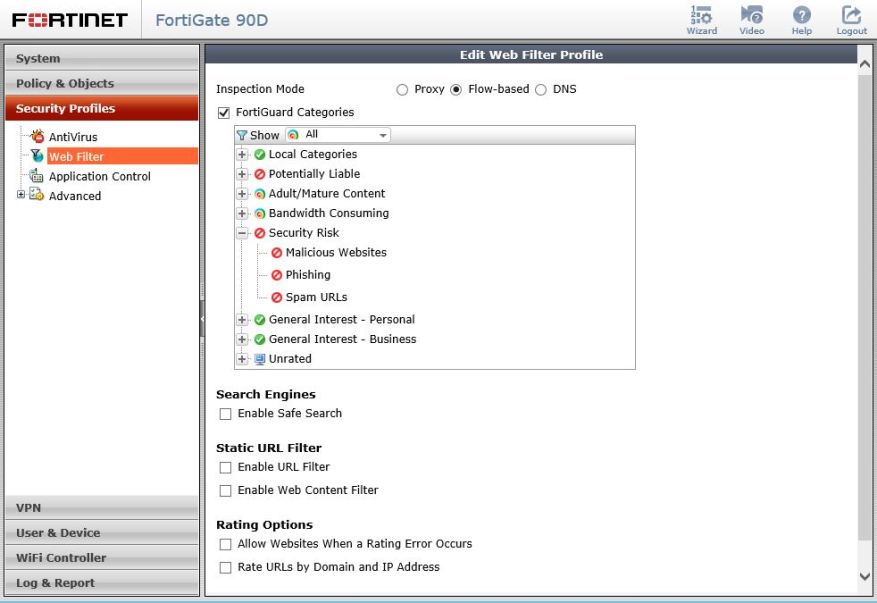
Thousands of new websites are published each year, but you can reduce risk greatly whether or not you decide to filter other categories. Fortinet is the current darling with regulators for strong security features comparable to Checkpoint or Cisco with easier configuration and lower price point.
4. Protect Devices with Cloud Management
We work as much or more today away from the office than at our desks. This fact means that on-premise software update and anti-virus systems often cannot provide the latest protection for most computer users.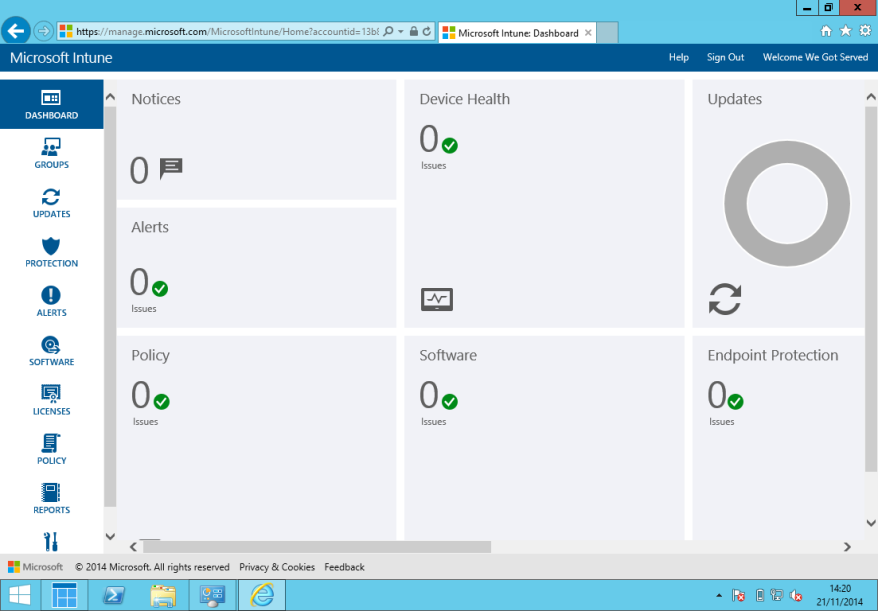
Cloud device management like Windows Intune enforces security policies and pushes software and anti-virus updates wherever a device connects to the Internet. Further, you have the capability of seeing real-time status of all computers to pinpoint an infection, run a malware scan, or wipe a device.
5. Remove Local Admin Privileges
Incredibly, some business applications still require the user to run as administrator. Nonetheless, the majority of us should not be in the Administrators group for a local machine to prevent applications running without authorization.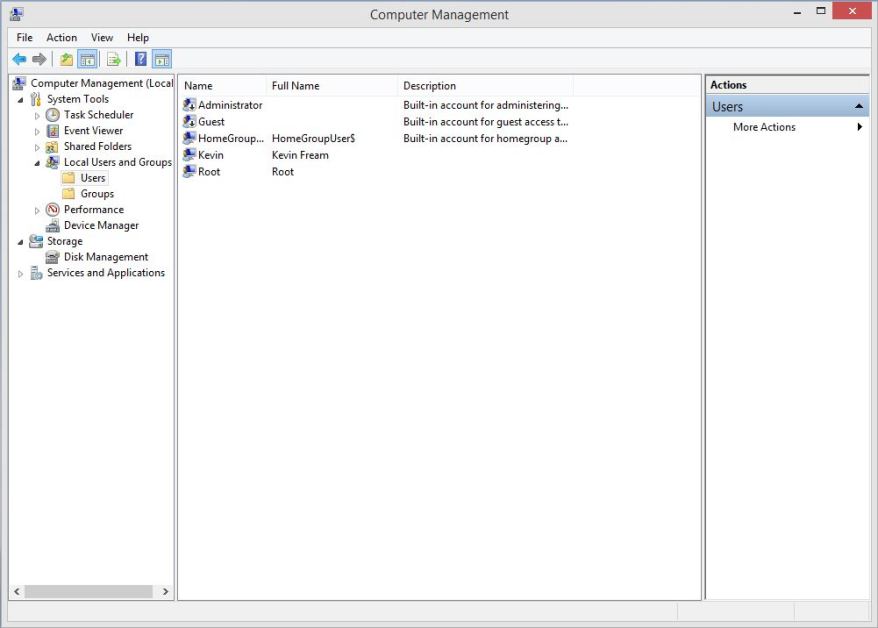
When new software is installed, you must enter the user name and password of a custom administrator account you created. This small inconvenience often prevents malware, as well as unintended system changes that can do irreparable harm.
For business network, such security is often the bane of both administrators and staff because software cannot be installed without administrator credentials. However, the current trend is simply to create a standard user account on the domain and add the account to the local administrators group on each workstation. Organizations then maintain productivity for staff, while enforcing reasonable security restrictions for the network.
That account can safely be given to users to download and install applications, without providing administrator permissions to the entire network. Since it is a domain account, the local admin password may be changed globally as necessary. More advanced permissions like the ability to join a workstation to the domain or install software from a file share may also be granted.
6. Enable System Restore
Having system restore points is a good practice to recover from malware and bad software or driver updates. Open System in the Control Panel and System Protection.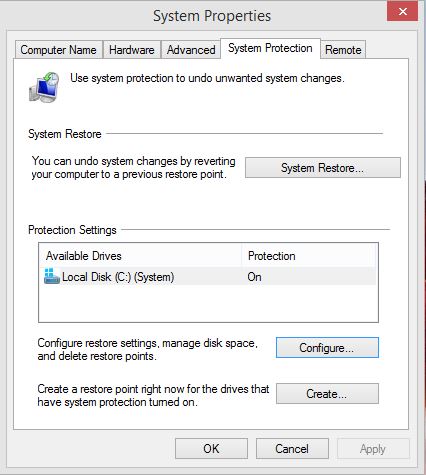
Make sure System Protection is on under the Configure button. Rolling back to a previous system restore point is often the fastest way to remove any malware.
7. Deploy a Software Restriction Policy
How to Avoid CryptoLocker Ransomware was one of the first articles about this subject published by Brian Krebs on November 1, 2013. After all this time, it’s truly surprising more enterprises haven’t deployed the referenced CryptoLocker Prevention Kit by Third Tier:- Create a Group Policy for Software Restrictions that disallows %LocalAppData%\*.exe with a description like “Block executables from AppData”.
- Test with a machine in a lab OU, but you’ll likely want to apply the policy to the entire domain after testing.
- It may take several restarts or GPUPDATE /FORCE and possibly as long as the following day before software restrictions are fully applied.
- Plan on several tests and expect the need to add exclusions for some legitimate programs like Java and Adobe that utilize the AppData path.
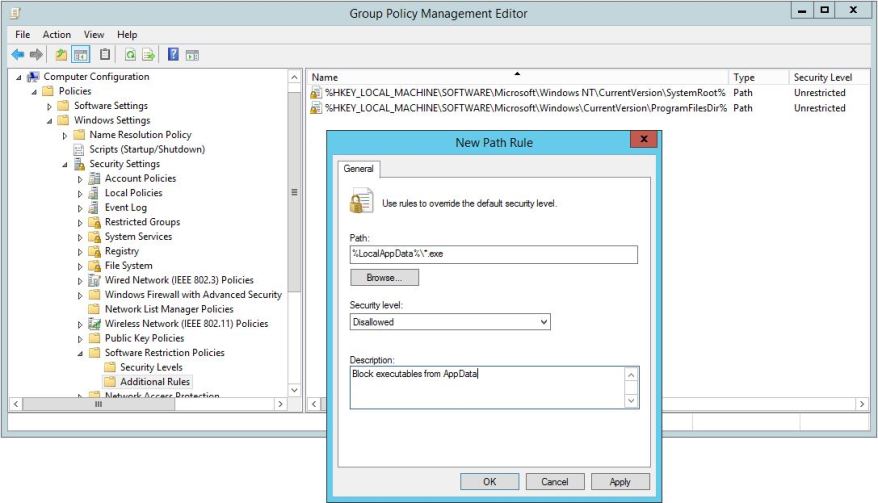
There is a tremendous amount of confusion on which path variables to use or add as %AppData% is not the same as %LocalAppData%. You must thoroughly test or you will prevent registered applications from running, but this strategy will help mitigate any type of virus outbreak. If you’re not familiar with software restriction settings, review the Microsoft TechNet article titled Software Restriction Policies.
8. Implement AppLocker for your environment
On October 25, 2013, Computerworld author Jonathan Hassell wrote CryptoLocker: How to Avoid Getting Infected that highlighted enhanced software restriction policies with Applocker. These advanced group policy rules are based on file attributes like digital signature, publisher, and file version.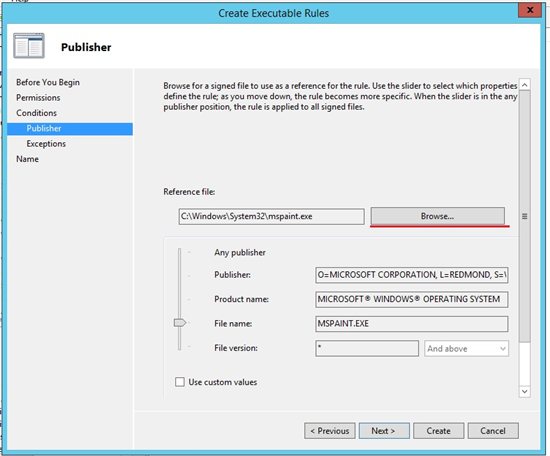
You can also deploy policies by security group or user, as well managing with Powershell. AppLocker Step by Step covers common scenarios and you can learn more with Microsoft Virtual Academy training like Securing a Windows 8 Environment.
9. Avoid Synching OneDrive
As revealed in OneDrive for Business Explained, it’s not practical to synchronize a terabyte of data on a regular basis. If you sync your OneDrive files or any other cloud service data to your local computer, then it is vulnerable to potential virus infection.
When you open current applications like Microsoft Office, OneDrive for Business is already one of the Open locations. Also, you can open OneDrive in Windows Explorer and add it to Favorites just like Desktop or Downloads. There are no sync issues and the link is a web URL that cannot be accessed by CryptoLocker.
10. Move Data to SharePoint Online
Just like mentioned above, data stored in SharePoint Online document libraries are accessed by web URL instead of a drive letter. Besides being inaccessible by CryptoLocker, SharePoint document libraries may also be used in Windows Explorer just like a folders in a network share only with a friendly name rather than a vague drive letter.
Unlike a file server, you actually get the user name and modified date and time on each file, along with previous versions and change alerts. Not only is the data more accessible, but you escape update and maintenance of another server.
11. Configure SAN Snapshots
Customers that have more than a terabyte of data should invest in a Storage Area Network (SAN). Besides centralized storage for multiple servers, file access is faster and storage expansion is easier. Unlike shadow copies on a server, SAN snapshots cannot be accessed by viruses and provide a quick way of restoring data changes or recovering from CryptoLocker encryption.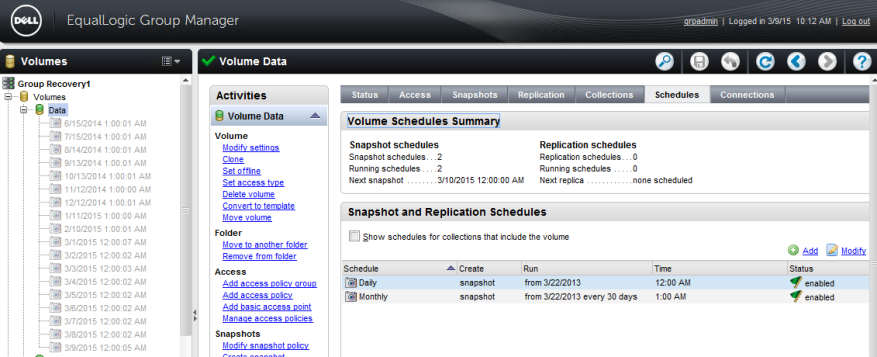
Snapshots provide regulation compliance for daily, monthly, and annual schedule retention. Snapshots also require less storage than local shadow copies and may also be replicated to external sites for offsite protection.
12. Verify Full Backup and Retention
In this new era of online backup, many customers fail to understand the type of backup being performed or whether restoration services are included. To present a lower price, many providers perform a limited incremental backup with no retention and fine print that restore tasks are the responsibility of the customer or billed separately.When catastrophes like CryptoLocker strike, unknowing customers may find out that restored data is some combination of files since online backup started (rather than current files from a specific date) and restore times may take several days instead of hours.
Cr.matrixforce.com
No comments:
Post a Comment